Why a BYOD Policy is Crucial for Securing a Hybrid Working Environment

The global pandemic has sparked a change in working practices like no other.
Arguably, the move to hybrid working, where employees split their working schedule between home and their workplace, was already on its way.
However, until February 2020, those ‘in the know’ were predicting that the change would be evolutionary, taking place over several years. Instead, the practice of hybrid working is here now … and it’s here to stay. It brings sharply into focus numerous benefits and challenges – not least the principle of BYOD, Bring Your Own Device.
The challenges revolve chiefly around the issue of security risk. Is your company encouraging a BYOD policy? Will your people be bringing their own smartphones, tablets, or laptops into the workplace? Then you need a BYOD security policy. Almost every employee comes to work with their own internet-connected device. This means a high potential than ever before for security risks to your company. For risks that you need to account for and protect against, having a cybersecurity strategy is key.
Your BYOD Policy is crucial for securing a hybrid working environment
BYOD has been far more prevalent than a few years ago. A 2014 survey from Tech Pro Research found that 74 per cent of organisations allowed employees to bring their own devices to work. By 2016, the figure had jumped to 87%. In many cases, they were relying on employees to use their personal smartphones to access mobile business applications. In fact, 45% of U.S. employees were required by their employers to use their personal smartphones for business purposes.
As an employer, you have two options:
- Embrace BYOD by enacting BYOD policies and security measures to make the practice a safer one.
- Ban BYOD entirely and find a way to enforce the ban.
The benefits to your company of a BYOD approach are clear:
- Reduced hardware and software costs
- Improved employee productivity
- Greater employee enjoyment
However, the practice will place extra responsibilities on your IT department. They will have to occasionally maintain the devices as well as ensure that your BYOD strategy doesn’t result in risks to either your network or your data.
What is a BYOD policy?
12 BYOD elements that your policy should cover:
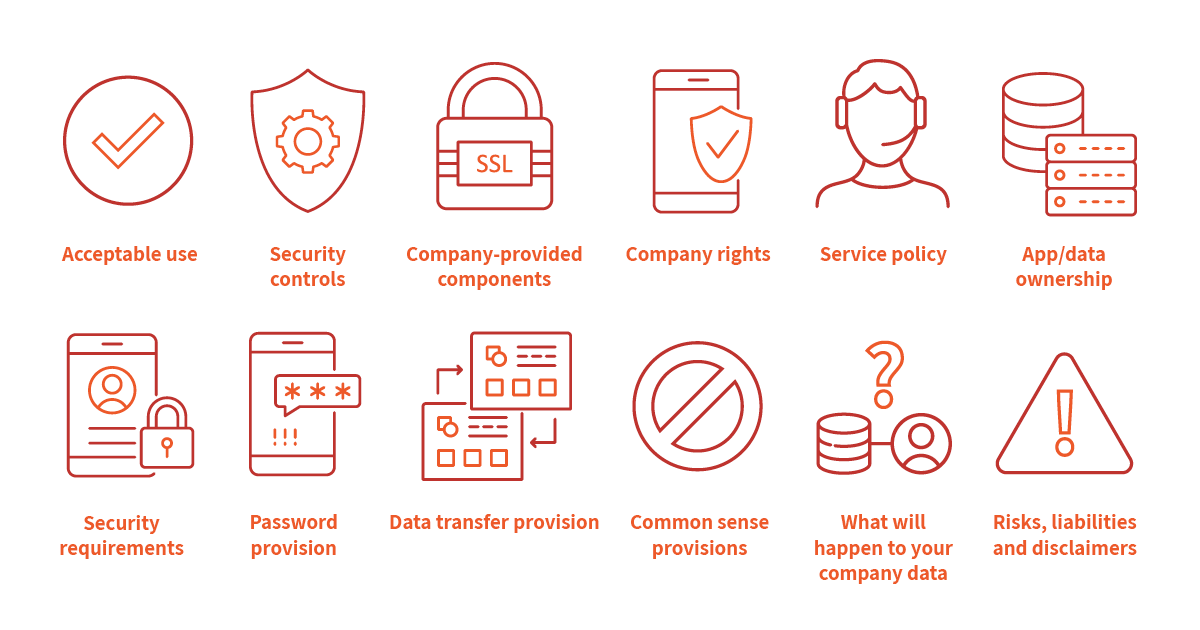
- Acceptable use – what applications and assets will you permit employees to access from their personal devices?
- Minimum required security controls for devices
- Company-provided components, such as SSL certificates for device authentication
- Company rights for altering the device, such as remote wiping for lost or stolen devices.
- Your service policy for BYOD devices – what IT support is available for employees connecting to your company network and support for applications installed on personal devices.
- The ownership of apps and data, as well as the applications that are permitted or prohibited and reimbursement (e.g., will your company reimburse employees a standard use fee, pay for certain applications or a portion of monthly bills?).
- It should also outline security requirements for BYOD devices (e.g., will your company provide a mobile device security application or will your employees be allowed to choose their own security solutions provided they meet your criteria?).
- Password provision – Your organisation will demand strong passwords. You might insist on regular password changes every 30 or 90 days, for example. What about 2-factor authentication? All these password considerations need thinking about.
- Data transfer provision – Data should be encrypted, password protected and only transferred on company mandated applications.
- Common sense provisions – such as restricting personal use when at work and banning use while driving.
- When an employee leaves your company, what will happen to your company data stored on their device?
- Risks, liabilities and disclaimers. Supposing company data is lost or leaked from your employee’s device, who will be liable?
How to set up a BYOD policy that works for everyone in the company
The first step, as with any change to any aspect of company policy, is to communicate – to ensure stakeholder and employee buy-in. Otherwise, you risk disenchantment and disengagement.
Your stakeholders will be key to the policy planning process, providing a variety of perspectives from various departments and interests within your organisation. Executives, HR, finance, IT and the security team – all need to be involved in the development of your BYOD policy.
Employee input matters
Employee input is vital for generating a BYOD policy that works. Only consider the needs of your company, and you’ll be asking for trouble.
Begin with an employee survey – an efficient way to gain data on the devices your employees use. Find out about what your employees see as advantages and disadvantages of BYOD. Do they harbour concerns about their privacy?
Consider your technology capabilities
It’s critical to ensure that you have the appropriate technology. An evaluation of your current capabilities will help to identify and fill these gaps to ensure a successful BYOD policy.
We’ve covered here just a handful of the factors you need to consider when developing your BYOD policy. You need to take on a multi-faceted approach that addresses the potential risks while minimising intrusions on employee privacy and usability.


